What Is a Proxy and How Does It Work?
Ever wondered how your device connects to the internet while keeping your identity hidden? A proxy server plays a crucial role in this process. It acts as a middleman, shielding your device from direct internet exposure and providing an extra layer of security.
In this guide, we’ll explore what a proxy server is, how it works, and the different types available. We’ll also delve into its benefits and real-world applications, helping you understand why these servers are essential for online privacy and security.
What is a Proxy?
Simply put, a proxy server acts as an intermediary between your computer and the internet. Instead of connecting directly to a website, your request is first routed through the proxy server. It then sends your request to the target website and returns the response back to you. This additional step can help mask your IP address, enhance privacy, and provide various other benefits.
How Does a Proxy Work?
A proxy server acts as an intermediary between your device and the internet, improving privacy by masking your IP address with its own. When you make a request online, it first goes to the server, which then forwards it to the target website. The website’s response is sent back to the proxy, which finally delivers it to you.
So, basic operation goes like this:
Client-Proxy Connection: When you connect to the internet through a proxy, your request is first sent to the server.
Proxy-Target Server Connection: The proxy forwards your request to the target website, acting as an intermediary.
Target Server Response: The target website sends its response back to the proxy server.
Proxy-Client Response: The server then forwards the response back to you, completing the process.
These servers also offer advanced features like encryption for secure data transmission, caching to enhance load times by storing frequently accessed websites, and load balancing to distribute traffic across multiple servers. They provide anonymity, protect against cyber threats, and can filter content to block unwanted websites. Additionally, they can host firewalls to prevent hacking attempts and malware infections.
Types of Proxies
There are various types of proxy servers, each offering different levels of anonymity and functionality.
Anonymous Proxy
This type conceals your IP address while disclosing its proxy status, providing basic anonymity and speed, though it may encounter access restrictions.
High Anonymity Proxy
Also referred to as elite servers, these not only hide your IP address but also do not reveal their identity, offering a higher degree of anonymity, albeit potentially at slower speeds.
Transparent Proxy
This type reveals both your IP address and proxy status and is commonly employed for content filtering, but it does not provide any privacy benefits.
Tunneling Proxy
A tunneling proxy, or gateway, is a server that passes requests and responses without modification.
Forward Proxy
A forward proxy serves as an Internet-facing entity that retrieves content from a wide array of sources across the Internet.
Reverse Proxy
A reverse proxy acts as an Internet-facing service designed to safeguard and regulate access to a server on a private network, typically performing functions such as caching, authentication, load balancing, or decryption.
Proxies, VPNs, and Beyond
Proxies and VPNs
While these servers and VPNs (Virtual Private Networks) may seem similar, they serve different purposes. Proxies primarily route your internet traffic through an intermediary server, masking your IP address and providing some level of anonymity. However, they don’t encrypt your data.
On the other hand, VPNs encrypt all your internet traffic, providing a more secure and private browsing experience. This makes VPNs ideal for sensitive activities like online banking. While proxies are generally faster due to the lack of encryption, VPNs offer a higher level of security.
Proxies and DNS
DNS, or Domain Name System, translates human-readable domain names (like www.example.com) into IP addresses that computers can understand. While DNS itself isn’t a privacy tool, certain DNS services offer features like blocking malicious websites and preventing DNS leaks.
Using a DNS service in conjunction with a proxy or VPN can enhance your online security. For example, DNS over HTTPS (DoH) encrypts DNS queries, adding an extra layer of privacy.
Proxies and Fingerprinting
Fingerprinting is a technique used to identify a specific device or user by analyzing its unique features. These features can include hardware specs (like CPU type and screen resolution), browser settings (such as language preferences and security options), installed plugins, and even specific behaviors like typing patterns and mouse movements. This detailed information can be used to track a user’s online activity across different platforms, tailor advertisements to match their interests, or even carry out targeted attacks that take advantage of individual weaknesses. As technology evolves, fingerprinting methods have become more advanced, making it a powerful tool for both marketers and cybercriminals.
Proxies serve a different yet equally important purpose. They are designed to mask a user’s IP address and other identifying information, making it significantly more challenging to fingerprint a device. By routing traffic through an intermediary server, they can effectively shield a user’s online presence, thereby enhancing privacy and complicating tracking efforts. Additionally, proxies can be employed to bypass geographical restrictions and access content that may be blocked in certain regions. This is why using a proxy is considered a vital component of antidetect technology, as it provides an extra layer of security and anonymity in an era where digital privacy concerns are paramount.
Mobile Anti-Detect with Proxies
Mobile antidetect solutions are really on the rise and are starting to take over the market.
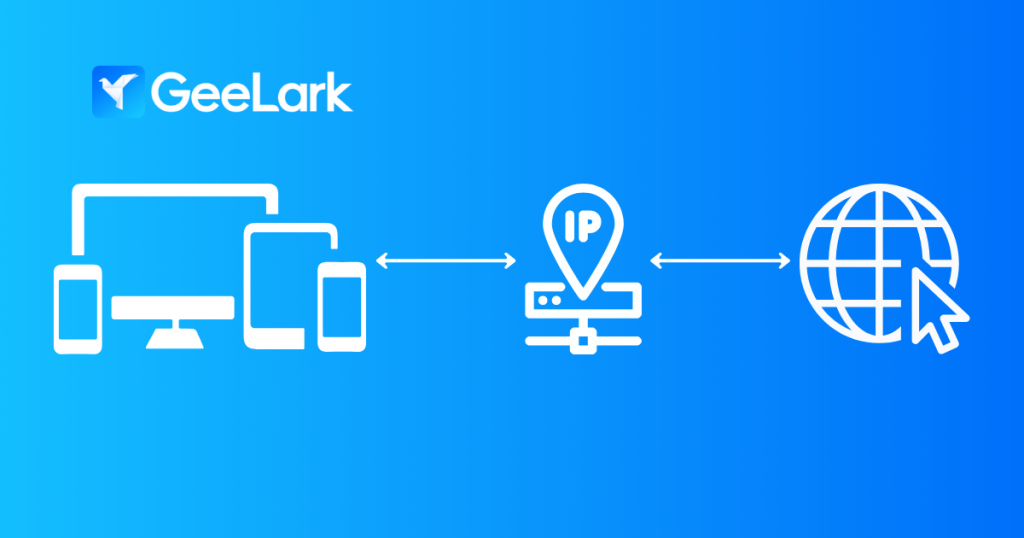
A cloud phone is an Android device hosted in the cloud, offering smartphone functionalities without physical hardware. GeeLark partners with cloud phone providers, allowing users to rent cloud phones through the app. Users must select a cloud phone when creating a profile, which then enables app installation and task execution like a regular smartphone.
Just like traditional antidetect browsers, a cloud phone for mobile antidetect needs proxies to work properly. An anti-detect environment will help you change your device information, while these servers will change your IP address. By combining these two, you can significantly boost your chances of successful spoofing.
The difference here is that cloud phone profiles provide an entire Android environment, much like physical devices. Unlike an antidetect browser, cloud phones expose users to a wider array of mobile-first multi-accounting opportunities.
How to Set Up Proxies in GeeLark
Before you create your cloud phone profiles, you need to set up proxies first. Here’s a simple guide to help you do that.
- Choose the appropriate type of proxy.
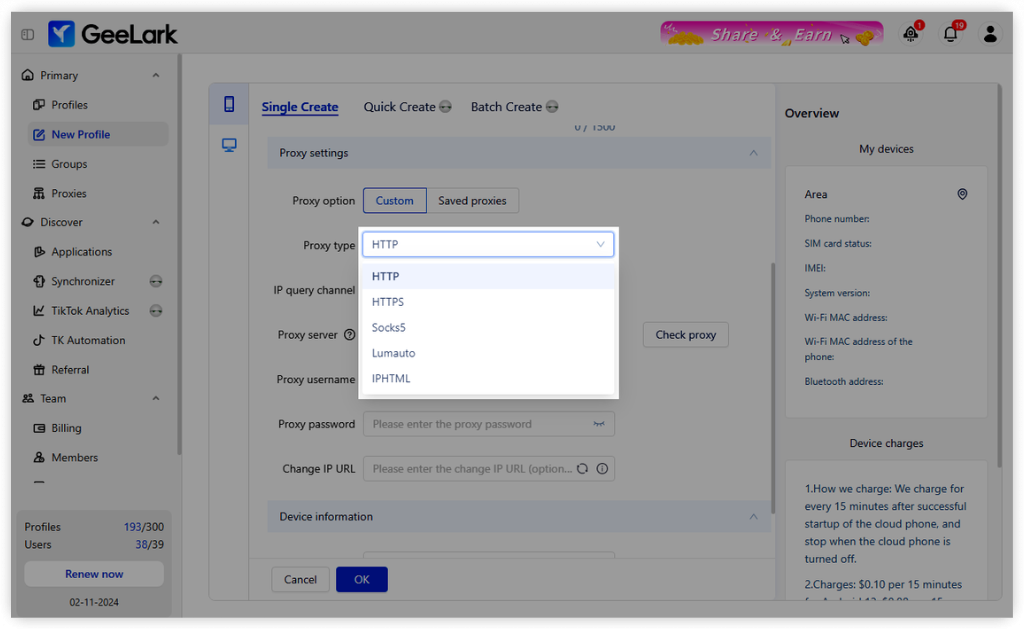
- Set up your proxy settings in GeeLark to ensure seamless integration with your mobile device.
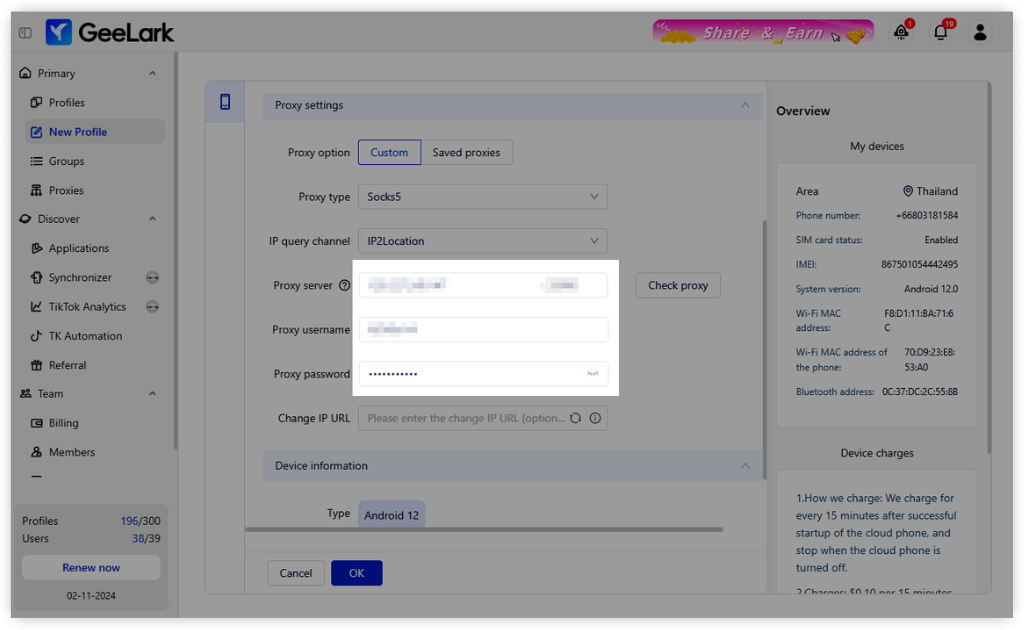
- Click on Check to verify the connection.
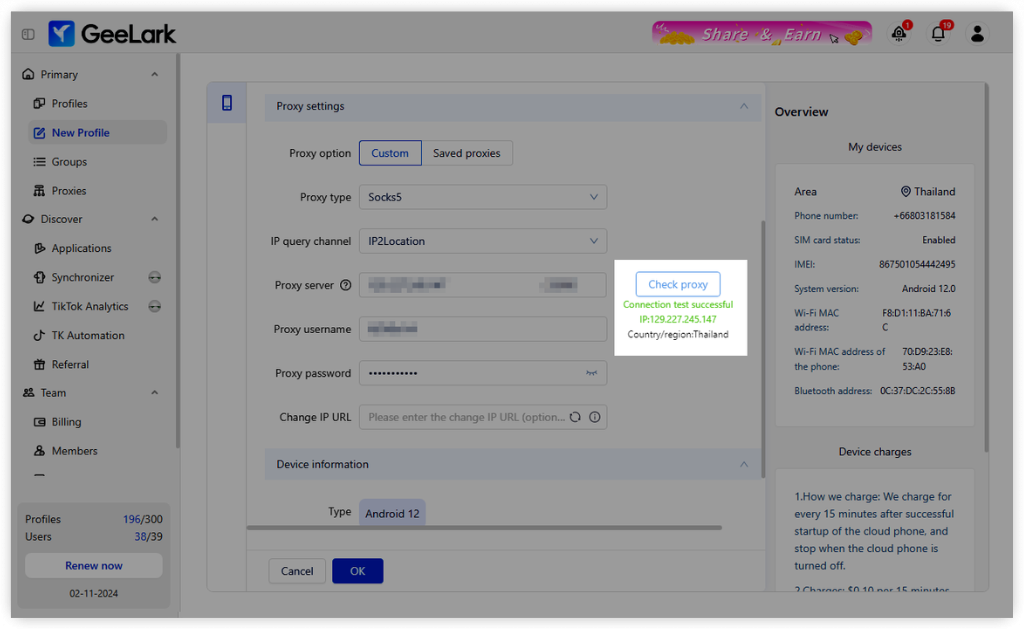
All set! Just click OK to finalize your settings, and you can start using your cloud phones now.
You can easily check your proxy list and their configuration info in the Proxies menu. Plus, if you’re looking for faster product hunting, you can find these servers in the More resources section right in the GeeLark app.
FAQs
Is a VPN a Proxy?
A VPN and a proxy are similar in that they both can mask your IP address, but they function differently. A VPN creates a secure, encrypted tunnel between your device and the internet. A proxy acts as an intermediary between your device and the internet for specific websites or applications. VPNs offer a more comprehensive and secure solution for privacy and security, while proxies can be useful for specific tasks or applications where IP masking is the primary concern.
What Happens When You Set a Proxy?
When a proxy is set up, it acts as a middleman that relays requests to the resource you want to access. The server then gets the results and sends them back to the original requester. Importantly, the requester does not communicate directly with the resource being accessed.
What Is the Difference Between IP and Proxies?
Think of an IP address as your unique online address. It identifies your device on the internet, allowing other computers to communicate with it. It’s like your home address, but for the digital world. Proxies act as intermediaries between your device and the internet. They mask your real IP address, making it appear like you’re accessing the internet from a different location. This provides privacy and security benefits.
Why Proxies Are Needed for Anti-Fingerprinting?
Fingerprinting is a technique that identifies users or devices by analyzing unique features, making it useful for tracking online activity and targeting advertisements. In contrast, proxies mask a user’s IP address, enhancing privacy and complicating tracking efforts. They also allow users to bypass geographical restrictions.